After quite a hiatus, again, I've produced a new mixtape: Beautiful Plumage. This one compiles new rock music from the past five years, in an attempt to disprove the eternal "rock is dead" meme.

After quite a hiatus, again, I've produced a new mixtape: Beautiful Plumage. This one compiles new rock music from the past five years, in an attempt to disprove the eternal "rock is dead" meme.

I'm working on a somewhat intricate C++ project (a persistent storage manager) that internally uses a lot of different integral types: page numbers, page offsets, page-cache indexes, bucket indexes, hash codes, transaction sequence numbers... It's very easy to get these mixed up, especially by passing parameters in the wrong order when a function takes more than one of these types; the results of that would be pretty bad.
It would be great if I could declare each of these as a different type, and the compiler would stop me from assigning a value of one type to a different one. The Nim language has an easy way to do this: I can declare type PageNo = distinct int and the "distinct" keyword tells the compiler to forbid implicit conversions between PageNo and any other integer type.
enum classIt turns out C++ can do this too, it's just not as intuitive. The secret is enum class. Added in C++11, this is a more restrictive version of the familiar C enum, which cannot be …
I've completed the necessary surgery to attach the Netlify CMS to my blog, and I'm writing this post in the web-based admin UI. Exciting!
Now maybe I'll actually post here...
At dawn came the pig truck, driving itself in from over the hills.
By the time it reached the jail, the prisoners were lined up, resigned, watched by the armed guards in their towers.
Cleaned and shaved, naked and divested of names, they were human no longer.
Dust rose and fell as the long blank truck pulled up, the back springing open by itself, the ramp dropping to the ground.
Every prisoner looked into the gloom within, weighing the uncertain death that awaited beyond against the certain death from above should they run.
Forward they filed, up the ramp, into the gray steel interior, the pen built for holding the animals called pigs, before the war.
Guns watched them in here as well, swiveling silently from high corners next to blank-gazed cameras, monitored by no one.
Her neck itched, in back, where she could feel guns trained on it; she was used to being under the eyes of guards, but this blank machine space unnerved her.
I could still run, she thought; the doors are still open.
Jumping down, dashing and weaving across the parking lot, shot down before reaching the barbed wire — bleeding out on the asphalt — thrown into a furnace, uneaten; now, would that be better or worse?
Knowing what she knew, the one edge she possessed, a secret long lost: could that really save her; could she trust it enough to endure in this car that stank of metal and death? …
She was a worker, that’s all. A courier. Pick it up here, carry it a long way, drop it off there. It was a dull job, but it meant she didn’t have to think much, which suited her. And everyone she knew worked the same job, so it was easy to share in-jokes and gossip and complain about the conditions.
Her people had no vehicles, no roads, no pack animals. But they knew all the trails throughout the valley and the forest, kept them clear and well-marked. They had a far-flung civilization, and their city depended on resources from the outside, so there was always food being carried in, and always a need for strong workers to haul the heavy loads.
She never looked up. She kept her eyes, her senses, on the trail ahead. Often the trail was crowded, and the view was just the person in front of her. She never looked up! Why not? Until one day something in her mind lifted her eyes, and she noticed the blue as never before. Stopped for a second, lost her rhythm, and the worker behind her collided and cursed. …
Journaling is a style of blogging that's gone out of style lately, for some reason, but it's dear to my heart, and to many of my friends'.
Journaling is exemplified by LiveJournal, which has a long proud history as the first social network and possibly the first turnkey blogging system (begun in 1999, it slightly predates Blogger.) LiveJournal still exists, but it's a shadow of its former self. The UI and functionality are stuck in an early-2000s timewarp, and worse, most of the users are gone, having decamped to Twitter and Facebook.
So what distinguishes journaling?
I'm afraid of a lot of things. Or, I'm often afraid of things. I have some issues with anxiety. The anxieties aren't constantly in my way; they're more like electric fences that keep me in line. I can go through my everyday life without thinking of them, but when I venture outside what I'm comfortable with I start to get crackles of sparks down my spine and in the pit of my stomach, and then usually I back away. So the anxiety doesn't have to get very intense: it does its job by merely hinting.
The monsters in my Anxiety Closet are only trying to be helpful, really, only trying to keep me safe. To put it in terms of moody '80s pop music: if you go to a club and you leave on your own and you cry and you want to die, you might in the future come up with good reasons not to go and repeat that disaster. Even if it just happened once, years and years ago. But as the same source put it a few years later, shyness can stop you from doing all the things in life you'd like to.
Last week I went to a conference, CocoaConf. It was in Portland, nominally speaking, although all I saw was the airport (nice carpet!) and the hotel a mile away. I think I spent five …
They were easy enough to mistake for sheep at a distance — white, fluffy, contentedly grazing — especially in the pre-storm dimness. It was when he got closer to them and saw their body shapes and the way they were eating that Laurence began to regret coming to the farm. As he watched, the nearest animal sheared off a half-dozen dandelions with its mandibles, squirted some sort of digestive ichor on them, and began rhythmic movements of its mouthparts.
“Mouthparts”, he said to himself. There was something disturbing about the very word, but much less so than seeing them in action close-up. He could see the shiny black carapace beneath the white fur now, and the huge compound eyes reflecting the first lightning. He lost his nerve and ran back across the field before the thunder hit.
“Why not regular sheep?” he asked Mo as he approached. “They’re traditional. Bucolic. We’ve raised them for thousands of years, right?” …
Well, it's the same blog, I've just replaced Jekyll with Hugo. If I've succeeded, you won't be able to tell anything's changed.
Every couple of years I go through this ritual of porting to a different blogging engine. This blog started out as handwritten HTML, then it went through Movable Type, Drupal, WordPress, Jekyll, and now Hugo.
Each iteration is usually an improvement, but to be honest, the main reason is to have a chance to mess with Web Stuff for a while. My day job is more about lower-level app code (Objective-C, C++, Go), which sometimes feels far away from what The Cool Kids are doing. So these makeovers give me a chance to reacquaint myself with HTML5, CSS, YAML, the templating engine du jour, Ruby, rsync, and so forth.
I'm at a computer lab [probably the one from college] and have written an entire email client app in a day. I'm excitedly showing it off to everyone. It's kind of glitchy but I can pull up my real emails, including spam.
The app is also, simultaneously, made out of a 2-liter soda bottle. It starts out crushed, and expands and fills with water as it launches. Unfortunately there are some cracks that water squirts out of. I explain that I am going to patch them soon.
People are pretty impressed that I wrote this in a day, but I point to some fat binders lying on the desk and tell them that I have a bunch of libraries I wrote earlier that helped me build the app.
_(Inspirations: Obviously there's the social network app I want to write that I posted about a few days ago. A friend asked me yesterday how it was coming. Also yesterday, Jed in fact wrote a pretty decent Tetris game in one day on the iMac. Plus, obvious visual pun about "memory leaks". And I'm increasingly frustrated with the poor quality of Apple's Mail app on 10.9 and wouldn't mind a replacement, though I'm not really going to write my own.) …
Modeling a social networking system like LiveJournal or Facebook in a JSON-document-oriented database like Couchbase [Lite] or CouchDB isn't hard. Here's a basic schema that I've been playing with for a while.
Top level items are document types (generally distinguished by a reserved type field), nested items are properties.
Here's my most recent music mix, "Forest Wire", all music from 2013. This mix is dedicated to my brother-in-law who builds guitars but nonetheless appreciates electronic music. It starts and ends ambient, but builds up into dub and K-pop and jungle and other styles.
(Née TouchDB, née Couchbase Mobile) Mobile syncable NoSQL database for iOS. My work project in one way or another since I started at Couchbase in mid-2011. I'm still having fun working on it.
The companion piece -- the glue that lets Couchbase Lite sync with Couchbase Server. It's been challenging and educational and boundary-stretching, and part of me is sick of working on it because the secret is I'm not a big-data guy. I've known for years that I like working on apps better than on servers. But this project had to be done, and I think I've done a good job of it and learned a lot.
I’m looking for some more beta testers for a font preview/management utility I’m working on. I've been frustrated by not having a good visual way to browse my font library, so I wrote my own. It’s called Jackdaw.
If you have a sizable font collection, choose (or just ogle) fonts on a regular basis, are willing and able to send bug reports/crash logs/suggestions, and are running OS X 10.8 or 10.9 ... then you should totally sign up. (Bonus points if you recognize the reason for the app name!) Testers who send useful feedback will get a free license for the finished app.
If you're interested, send me an email at "thought-palace" @ this domain.
This blog kind of ground to a halt in 2011. I think the final straw was having my WordPress hacked and many of the posts defaced with spam links. After that I swore a mighty oath not to have any further trafficking with the wickedness of PHP.
But I still miss blogging (proper blogging not tumblr). Sometimes I have things to say! And apparently back in the day a few people even used to read things I wrote here, which is nice to think about.
I've brought the blog back to life in a new form, using Jekyll, a static site/blog generator. It's been around for a while, and I've fooled around with it before, but it never had any decent themes and I was discouraged by the effort it would have taken to build my own from the ground up. But then last weekend I discovered HPSTR, which is exactly what I wanted, a lovely theme with nice touches like scalability from smartphone screens up to big displays. So I installed it, spent a happy day or two hacking away at the fonts and layout, and here we are.
[I just posted this to the Couchbase Mobile community mailing list.]
TouchDB is a project I’ve been feverishly working on for a few weeks. It’s an investigation into the feasibility of a CouchDB-compatible database rewritten from the ground up for mobile apps. The comparison I like to make is that “if CouchDB is MySQL, then TouchDB is SQLite”. In fact, it uses SQLite as its underlying storage engine. You can read a longer justification for it on its wiki, as well as an FAQ and design document.
— It speaks CouchDB’s replication protocol. I’m pretty serious about
that; I’m even documenting the
protocol.
— It also understands a large subset of the REST API, enough so that it
works with CouchCocoa. I’ve got a clone of Grocery Sync working as one
of the demo apps in the project.
— The current implementation is for iOS. If the investigation pans out
we’ll port it to Android, and possibly other platforms.
TouchDB is certainly not ready for prime-time yet, but here are some current statistics to whet your appetite: …
I gave another talk about Couchbase/CouchDB at the Keeping It Realtime conference this week in Portland. This one is titled “_ch_ch_changes: CouchDB/Couchbase Notifications And Replications”, and the slides are now up on slideshare.
I had a great time. The conference itself was pretty exciting, even if some of the content was over my head (I’m not primarily a web developer, server-side isn’t how I roll, and I’ve only just started learning about node.js this week!) Plus: Portland. OMG, I love Portland.
My new employer is doing well:
MOUNTAIN VIEW, Calif. – August 10, 2011 – Couchbase, the leading NoSQL database company, today announced it has secured $14 million in a Series C round of financing led by venture capital firm Ignition Partners with participation from the company’s existing investors Accel Partners, Mayfield Fund, and North Bridge Venture Partners. The company has also reserved an additional $1 million for investment from strategic customers and partners. The new funding will be used to further invest in NoSQL product development, support the adoption and growth of Couchbase in enterprise organizations, and support international expansion. …
August in Los Angeles was bone-dry and dusty, but he left it behind in the parking lot as he made his way through the series of three doors, heavy and white, and into the frozen refuge of the ice bar. He was known, there, and the hostess greeted him with a sealskin robe, slipped over his shoulders before he had time to start shivering. The tip of her elegant nose felt icy against his own.
There was room for one more at the bar, and at a nod from the chef he took the seat gratefully. One often had to wait, stamping feet to ward off the cold. The chef slid the amuse-bouche before him as he unfolded his napkin, and it was exquisite in appearance: a translucent carpaccio of walrus blubber sprinkled with snowflakes. The snowflakes were not unique, in fact they came in precisely two shapes, one sprinkled on the left side of the dish, the other on the right. They made not-quite-imperceptibly different crunches as he ate them. It was touches like this that had made the chef’s name when he was but a young man just arrived from Nunavut. …
I’ve just released a new open-source project, a small one — Fudge-Cpp, a fast C++ library for reading and writing Fudge messages.
I hadn’t heard of Fudge either, till a few weeks ago, but it’s a type of thing that’s always interested me: a generic structured binary data format. A quick elevator pitch would be “it’s sorta like JSON, except more compact and faster to parse”. (It’s also sorta like Mac property-lists, YAML, etc.) So, it lets you turn collections of scalars, strings, arrays and dictionaries into a standardized blob of data that can be sent over a network or stored on disk or whatever.
From the Fudge website:
"Fudge is primarily useful in situations where you have:
No again, I will not show you what’s under the bandage on my arm. I won’t even look myself, anymore; it’s gotten too disturbing. I mean, the wound hasn’t changed, but every time I look at it it bothers me more, takes me longer to stop shivering. I keep wanting to touch it.
Listen: Did you ever play Shock City? I’m not trying to change the subject; hear me out. I played the hell out of that game when I was twelve, and I always wondered what was inside all those buildings you couldn’t get into. There were only eight buildings with working doors in the whole game, with all kinds of things to explore and enemies to stalk in each one; so if you could somehow get into the other hundred or so buildings, what would be inside them? Could you play them too?
I know, I was pretty dumb back then. I didn’t understand the way the world works.
Finally someone told me about a hack to get into any building. It exploited a bug in the hit detection: you had to run at a corner and jump right at it. If you got the position and angle just right, you’d slip through the join between the two walls and be inside. People were using this as a cheat to get into the higher levels early, but all I …
I’ve never figured out whether I prefer Python or Ruby, so I’ve written things in both languages. Sometimes I start in one, then change my mind and decide I’d rather use the other. Unfortunately, changing over is painful, even though both have fairly similar syntax. For instance, converting to Ruby means inserting zillions of “end” statements!
Having a need to do this recently, I lazily looked around for a script that would do the grunt-work of Python-to-Ruby translation. I couldn’t find one, so I ended up writing one myself. And I’ve uploaded it for the benefit of others who might have the same need, and who might even improve it.
So here it is: py2.rb. Use it wisely. In particular, pay attention to the caveat found in the file’s header comments:
This script just does the obvious, easy transformations, giving you more time to work on the harder ones :) It is NOT a real parser, just a bunch of kludgy regex operations, so it can’t do anything fancy. It may get some things wrong, and won’t even attempt some other things that it’s very likely to get wrong. The output will definitely have to be hand edited by someone familiar with both languages, before it can …
Brent “NetNewsWire” Simmons raises the idea of an open protocol for syncing RSS/Atom subscriptions, that is, a way of keeping multiple local newsreader apps (like on a Mac and an iPhone) in sync with each other, so that they share the same set of subscribed feeds, and remember which articles have already been read. You can think of it as “IMAP for RSS”.
NetNewsWire already does this using Google Reader as an intermediary, and Apple’s PubSub framework (which is what Safari and Mail use) shares the read/unread state using MobileMe. But it would be nice to have an open protocol.
I have some experience with this, having implemented the sync system used by PubSub. It’s an interesting problem — you might think I would have just used Apple’s SyncServices, and it’s true that it would have worked great for the subscription list, but it doesn’t scale well to huge numbers of rapidly-changing “read/unread” flags.
I have two suggestions (which I would have made on Brent’s blog, except he doesn’t allow comments anymore.) …
Every year the Albums Of The Year lists seem more and more removed from my experience. (Most of the time I haven’t heard a single album on the list.) Worse, we’re now getting into the Of The Decade lists, making me realize how long this has been going on*. If you ask me the top albums of the ’80s or ’90s, I don’t have too much trouble rattling off a bunch of names. But this decade? I get confused and have to start thinking hard and looking through the back covers of my mix CDs. Why is that? [Ed.: it’s because you’re getting old. Duh.]
Let me start with this year, 2009. What was good? Hm; my prosthetic brain units at iTunes and last.fm tell me that it’s:
• Dysrhythmia, "Psychic Maps" [jaw-dropping instrumental math-metal, will have you banging your head in 7/13 time.]
• Isis, "Wavering Radiant" [post-metal? huge lowercase-‘p’ progressive epics. so good I’m willing to overlook the cookie-monster vocals.] …
Call the roller of big dice,
The long-haired one, and bid him whip
On kitchen tables consecutive 18’s.
Let the fighters dawdle in such armor
As they are used to wear, and let the mages swap
Delicious spells from last month’s Dragon.
Let a fumble be finale of its caster:
The only emperor is the dungeon master.
Take from the manual of monsters
Painted with three crude beasts, that sheet
On which I enumerated his stats once,
And spread it so as to cover his face.
If his bag remains, rifle his hoard
To see who gets his precious +6 sword.
Light the lamp to run away faster.
The only emperor is the dungeon master.
Farhad Manjoo writing in Slate about Google Wave:
The trouble is, everything you type into Wave is transmitted live, in real time — every keystroke was getting sent to Zach just as I hit it. This made me too self-conscious to get my thoughts across.
… Maybe I should just delete what I’d written and say, “Twitter works because it’s simple.” But I couldn’t do that, because Zach was watching me. He could see me struggling right now—he could see that I’d gotten myself stuck in a textual cul-de-sac and that I was desperately searching for a way out without looking foolish. Now I saw Zach beginning to type: “Don’t let the live-typing get you down!” The game was up; what was the point of making a point now? I ended my thought clumsily and then resolved never to attempt to say anything very deep on Wave. …
So far, this blog’s main claim to fame has been as the #2-ranked Google hit for [apricot jam recipe]. But that’s no longer enough to sustain my extravagant lifestyle, so I’m following the next most obvious business opportunity: Elephant jokes! These were huge (the jokes) when I was a kid, but they seem to have been largely forgotten, which is a shame. I tested them out on my kids today, and they still work fine.
These jokes are, admittedly, about as unoriginal as my jam recipe. And the list was generated roughly the same way as the jam, by picking pre-existing collections, cleaning off the typos, and boiling them down a lot. In fact, I’ll lead off with an apricot joke:
Q: How is an elephant like an apricot?
A: They are both gray. Well, except the apricot.
Q: How can you tell if an elephant is in the refrigerator?
A: The door won’t shut.
Q: How can you tell if an elephant has been in the refrigerator
earlier?
A: Footprints in the butter. …
I know, three weeks ago I said I was building me a B-Tree. I did build it, even the parts I listed under “What’s next?” in that post, and it works. But it became apparent there was a more urgent need for a hash table, for work-related reasons, so I switched gears to build one of those on the same principles.
The biggest principle is Append-Only Storage, as described in the prior post. So I thought back to the simplest on-disk hash table I know of — Dan Bernstein’s CDB — which is very clever, but read-only. I implemented something similar, and then mashed in the CouchDB-like approach of incrementally appending only the modified sub-components.
Initially I made the file a series of key-value pairs, followed by the hash-table index as an array of {hash code, position} structures, each of which pointed to the position of the corresponding key and value. Very simple. To save changes, I’d write out the changed pairs, followed by a new copy of the index. The problem with that was that the index gets large as the number of records increases, so with a 100,000-record file, changing even one record would append almost a megabyte. …
Last year I wrote a series of blog posts about a peer-to-peer system called Cloudy that I was developing. I was going up the stack, from messaging to identity, but didn’t finish documenting all the layers I’d built. I mostly stopped working on Cloudy after I went back to gainful employment, but I keep thinking about this stuff.
I’ve since heard about another unrelated project nicknamed Cloudy; and the whole term “cloud” has gotten so debased in the past year that it now stands for outsourcing to giant hidden server farms, which is the antithesis of what I stand for. So I’ve decided to use the name Lakitu instead. Nintendo fans will recognize Lakitu as a bit character in the Mario games — he’s a goggled turtle who rides a little one-seater cloud. This makes him an appropriate mascot for P2P technologies, I think.
[I’m sure Nintendo has a trademark on the character, but they don’t appear to have copyrighted the word “Lakitu”. He’s not even known by that name in Japan, where he’s called “ジュゲム” or “Jugem”. I have been unable to find out what “Lakitu” means or why they decided to use it in …
The other day I took it into my head to implement a B+tree. Why? Because they sound neat, and I’ve done hardly any serious programming with trees in my career. (Someone, I think Buzz Andersen, once noted that there are two kinds of programmers: those who do think in terms of trees, and those who do everything with hash tables. I’m in the latter camp.)
And also because I’m a big fan of CouchDB, and really admire its elegant storage model. It’s an on-disk B-tree — no surprises there — but the file is append-only, which both makes it impervious to crash-related corruption, provides nearly lockless concurrency, and makes it easy to access earlier revisions.
[In a nutshell: Updated data values or tree nodes are appended to the file instead of overwriting the earlier versions. Since updating a node changes its location, its parent node needs to be updated too to point to the new location. This recurses up the tree, meaning any change ends up with a new root node written at the very end of the file. In fact, when you open the file you find the root by looking at the very end. Since no data is ever changed, once you open the file you’re impervious to changes made by other writers since they don’t affect anything you’re looking at.] …
I got an iPhone 3GS yesterday (yes, it totally rules.) While setting up online account access for billing, AT&T had me enter a password.
There was one of those colored password-strength meters next to the text field, and it said the password I entered was “weak”. Alright, I changed it to add some commas and dashes.
Then I hit Submit, and was told that passwords can only contain letters and digits.
sigh.
Introduction: I wrote this as part of a reply on Apple’s bonjour-dev mailing list, then decided it might be worth publishing more visibly. I’ve found that Cocoa’s Distributed Objects technology is immediately attractive to many developers, while those who’ve used it end up finding that it’s much more complex than it looks. But I haven’t seen much written about the caveats of using it.
I am not saying “don’t use DO” or “DO is broken”! It has valid uses, and it works as designed. But you should be aware of the less-obvious complexities. If you have a single GUI app and a single background agent, that’s a great use-case. If the agent communicates with multiple apps (like the iChatAgent), things get trickier. If you’re going to use DO over the network, you’ve got to be really, really careful. …
I’ve been working at Google since last August. The Big G’s hiring process is rather weird — when you interview, it’s not for any specific team. It’s only after you get an offer that you decide which team to join, of the ones with open positions.
I decided on Google Sites, which I knew and liked from its days as JotSpot, a hosted wiki with some powerful features. It ended up not being the right place for me, for a couple of reasons:
I’ve always liked the Keychain technology in Mac OS X. Sure, the API is notoriously confusing and awkward, but the end-user benefits are compelling:
For the past few weeks’ worth of Copious Spare Time, I’ve been trying to get my MYCrypto framework, which is in part a friendly API to the Keychain, to run on iPhone. The iPhone has a Keychain API, but it’s a different API than the Mac OS one. At first glance it looks simpler and easier to use, and …
MobileOrchard just published a tutorial article by Peter Bakhyryev, describing a sample iPhone app called “Chatty” that acts as a simple peer-to-peer chat-room.
“In this tutorial, we are going to explore a simple chat application for the iPhone. It allows you to host your own chat room and advertise it on your local Wi-Fi network (in which case your app acts as a chat “server”) or find and join chat rooms hosted by other people on your network (acting as a chat “client”). Both announcement and discovery of chat rooms are implemented using Apple’s Bonjour protocol. The goal of this app is to show you how to use various networking-related frameworks available in the iPhone SDK version 2.x. The UI is minimal (consisting of only 3 simple views) - just enough to be able to play with the core functionality of the app without having to deal with complex UIKit code." …
“Some people have suggested that mental illness is a kind of adaptation to the sort of circumstances that will arise in the future. As we move towards a more and more psychotic landscape, the psychotic traits are signs of a kind of Darwinian adaptation.” —1998
Numerous studies have been conducted upon patients in terminal paresis (GPI), placing the author J.G. Ballard in a series of simulated auto crashes, e.g. multiple pileups, head-on collisions, motorcade attacks (fantasies of Presidential assassinations remained a continuing preoccupation, subjects showing a marked polymorphic fixation on windshields and rear trunk assemblies). Powerful erotic fantasies of an anal-sadistic nature surrounded the image of the award-winning novelist.
The feelings created by music are so strong, for me, but so ineffable. The problem of perception is usually described using color — how can we know if the visual sensation I call “red” is anything like the one you call “red”? — but only gets worse as you ascend to higher order perceptions, where even names become harder to apply. What do you call the feeling incited by “Guernica”, and even if you find the same words I would, is it the same feeling? And yet vision is our strongest, highest-bandwidth, most describable sense. We struggle to describe sound without using the technical terms of musicians, or vague metaphors.
It doesn’t help that so much of the music I like is so inward-focused: the guitarist gazing (not at shoes) at effect pedals, the producer sliding waveforms around a timeline, the listener bracketed in headphones like my picture above.
Everyone wants their experience of music to be shared. To play an instrument or sing for others, to blast the song from car speakers. To identify with music meant to shock, and use it to shock others. To attend a concert and know that those around you are hearing and feeling the same thing you are, right then: sitting following the intricacies of Bach, or exploding in a mosh pit. Drugs of many kinds help to collapse …
So, Web 2.0’s heyday is over, and somewhere out there, Web 3.0 is slouching toward us waiting to be born. What will it be?
There’s really no such single thing as “Web x”, of course. And all predictions are really just wishes. That being said, my wish is that Web 3.0 will be about distributed systems. To oversimplify:
Web 1.0 built up big brand-name websites with their own content — things written by them, or repurposed from the media companies that owned them, or stuff to buy.
Web 2.0 embraced “user-created content” and interaction between users. The content creation has become less centralized, outsourced to whomever wants to register an account and post stuff, but the sites managing, storing and serving the content are still centralized.
Web 3.0, I hope, will take the decentralization to the software, and the storage. Monolithic web apps run by huge server farms — Facebook, Blogger, Twitter, Flickr, etc. — will be at least in part supplanted by apps that users run locally (or at least ‘nearby’) and which share data among each other. …
The Pessimistic Form
The set of commands available in a toolbar (even via customization) is
restricted to those that are either:
(a) painfully obvious (New, Save, etc.), or
(b) useless to you (Save As EBCDIC, Post To CompuServe, Bilinear
Zeta-Regression, etc.)
The Optimistic Form
Combine this with the well-known principle that, while everyone uses
only a subset of an application’s features, everyone uses a different
subset. Conclusion:
To be useful, a toolbar’s customization UI should allow every single command in the application.
There are three difficulties that stand in the way of making every command available in a toolbar: …
I really don’t know how long I’ve been lying on the couch, watching the men on the TV. I don’t remember things so well anymore, since the accident. I don’t remember the accident either, but my friends tell me it was pretty bad. I have healed about as well as I’m going to, and though I don’t get around well, I can still think. In small doses.
The men on the TV gesticulate about some crisis or other; I can’t tell what, because the sound is off. They look angry — at me, at all of us, at themselves. Small text crawls across the screen above and below them. The TV men look very tired, too, as tired as I feel, and perhaps lost and afraid. I feel such sympathy; I would like to turn up the volume and learn more of their situation. Maybe I could ask one of my friends to.
Madeline is staring out the window. The window is next to the TV, it is filled with blackness, and speckly stars, and dim reflections of us. It’s night-time. Madeline’s gaze intersects mine somewhere near the empty center of the room. She is looking very intently into that blank space, at nothing I can see, and it makes me worry what might be out there. She is counting something; I know what that is, at least. I watch her lips move — she is up into the millions now. Some of us have nervous habits, some of us aren’t taking this ordeal so well. …
Matt Knox, a Ruby developer and repentant former coder for an adware company, explains how adware works. Really fascinating stuff, and quite scary from a security point of view.
“At the same time, we also made a virtual process executable. I’ve never heard of anybody else doing this before. Windows has this thing called Create Remote Thread. Basically, the semantics of Create Remote Thread are: You’re a process, I’m a different process. I call you and say “Hey! I have this bit of code. I’d really like it if you’d run this.” You’d say, “Sure,” because you’re a Windows process— you’re all hippie-like and free love. Windows processes, by the way, are insanely promiscuous. So! We would call a bunch of processes, hand them all a gob of code, and they would all run it. Each process would all know about two of the other ones. This allowed them to set up a ring … mutual support, right?” …
FYI, I ended up taking the position at Google. I started two weeks ago, and it’s been quite exciting, despite (or because of) the “drinking from a fire-hose” aspect of learning my way around the big G.
I’m on the Google Sites team. I’ve been interested in wikis for years, and now I get to actually work on one. (Although Sites, née JotSpot, is not a typical wiki.)
I could write a lot about my experience of Google so far. It’s quite an interesting place. Merely learning about how some of their internal systems operate has been jaw-dropping. (Do you have any idea how much hard disk space Google has? Or how many CPUs? Or how many search queries they handle? Unfortunately I don’t think I’m allowed to tell…)
For now I just wanted to say that I’m not in the job market anymore. Also, that I really like all the free food :-d
My Decktet is a thing of beauty. I even printed & assembled the box (an activity that took me back to my happy childhood days of making paper polyhedra models.)
The only problem is that the cards still have a faint sickly-sweet stink of toluene and acetone (from the plastic coating) even after I left them spread out on the floor for a few days. It’s quite unpleasant, not like the nice smell of new books, cars or boardgames.
Is this the papercraft equivalent of Code Smell
Sometimes it’s nice to make physical objects. It’s usually messier and more time-consuming than doing it on the computer, but in the end you have something you can actually touch.
Ever since I saw P. D. Magnus’s Decktet — a whimsical yet mysterious deck of cards for games or divination — I wanted one of my own. However, the Decktet is currently only available as a PDF, so any physical manifestation has to be of a DIY nature.

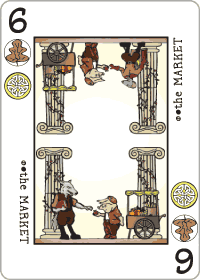
The deck has 36 cards (plus the optional “The Excuse”), of six suits, and its most unusual feature is that the number cards each have two suits. (There are also single-suited Aces and Kings.) This obviously adds a lot of interesting possibilities for games.
Magnus has given each suit a symbolic meaning, as well as a color, and done a good job integrating them into each card. For example, the Penitent (see above) combines the green color and violent connotations of the Wyrms suit with the orange and “decisive action and clarity of purpose” of Suns; while the Market combines Wood’s “gift of the earth … raw materials and food products” with Knots’ “craft, skill … commerce and money”. …
I’ve created a BLIP-Protocol mailing list on Google Groups:
Please join up if you’re interested in learning, using, re-implementing, improving, extending…
I’ve released the source code to my “BLIP” protocol implementation, as part of a project I call “MYNetwork”, for “Mooseyard Networking Libraries”. API documentation is available online, and you can check out or browse the source code from its Mercurial repository. For the really curious, there’s even a sketchy overview of the protocol’s wire format.
It’s working quite well for me in Cloudy; it’s been a while since I’ve found any outright bugs, although I know there’s more work to do on performance and features. It’s not production-ready code yet, but I think it’s ready for people to start using!
For now you can leave feedback in comments to this post, or by email to jens at this domain. If there’s enough interest, I could set up a mailing list.
Here’s the description of BLIP from the API docs… …
I’ve got my new BLIP protocol all implemented now. After my previous post on Monday:
Cloudy’s back up and running, and all its features work. So, that makes one week of effort to implement the networking layer from scratch (I started sketching and coding on Saturday). Really makes me regret spending several times that on the previous library — writing an Obj-C API, fixing bugs, adding features. Still, I’m sure all that experience helped me implement BLIP so quickly. …
…and which side of that line am I on? Not in general; just in respect to my latest decision in Cloudy. It’s the old “make vs. buy” trade-off, or “write vs. reuse” in this case: do you go with an existing library, even if it’s problematic, or do you write your own implementation from scratch?
What am I talking about? The networking code in Cloudy. From the very beginning I wanted to use BEEP, a generic and flexible protocol for sending request/response messages over a socket. It has good support for parallelism, nice abstractions like multiple channels and feature negotiation, and supports SSL.
The BEEP implementation I’m using is Vortex. It has the benefits of existing (there aren’t a lot of BEEP implementations around), being written in native code, and being within my capabilities to get running on Mac OS X. Unfortunately it’s also got a very complex and unintuitive C API, spawns lots of threads and calls my code from them (so I have to deal with thread-safety), and isn’t quite finished yet. So over the months I’ve put a lot of work into writing an Objective-C API, figuring out how to get that working reliably, and diving into the Vortex code to fix bugs and add new features. …
Stickies and I hadn’t spoken in a while, but it called me this morning to announce it’s made its acting debut in a music video! That was unexpected, to say the least, but it’s an exciting career move, and I had to congratulate it; it does a great job:
Stickies makes its entrance at 0:53, if you want to skip directly to it, but really the entire video (and song) are excellent. I just wish they’d used Stickies in the opening scenes instead of Word — face it, Word is over the hill, especially that old Office 2004 version. (Did you see the bags under the Office Assistant’s eyes? Stickies told me they dragged it straight out of the Betty Ford Center to shoot those scenes, and it couldn’t remember any of its lines even though they were right up on the screen next to it in giant print. It’s sad, really. At least it hasn’t OD’d yet like that pathetic paperclip.)
This seems to be a fan-made video, by the way; but I think it’s better than the official one. Now the question is: will Apple use this in a commercial? I think they should! …
Continuing from the previous Cloudy post …

The first time you connect to someone, how do you establish that digital identifier you’re communicating with is the human being you think it is? This is surprisingly difficult to do, because it’s prone to what cryptographers call the “man-in-the-middle attack”.
(Those of you already wearing tinfoil hats can skip past the general explanation, down to “What Cloudy Does”.)
First, consider the most obvious attack: simple spoofing.
Next I need to talk about networking; having an identity and minting certificates isn’t very interesting until you can connect to someone else.
When one Cloudy peer wants to communicate with another one, it opens a TCP socket to its IP address —
[Hang on, there are two issues I suddenly glossed over in that last phrase. First, how did this peer find out the others’ IP address? These are just random computers, not servers, so they don’t have their own domain names or even stable addresses. This is indeed a problem “y unstructure”to-peer network, but the solution involves things I won’t get to until the next installment, in an unfortunately but necessary violation of layering.]
[Oh, and issue #2 is that most home computers are now behind Network Address Translators (usually some kind of WiFi base station or broadband router), which means they don’t have their own real IP addresses and can’t receive incoming connections. Fortunately, most NATs now support protocols that …
Continuing from the previous Cloudy post …
At the root of Cloudy is the means for creating and establishing identity. A lot of peer-to-peer systems treat the peers mostly as interchangeable anonymous nodes, often deliberately so, but Cloudy is a social system.
The identity and security layers of Cloudy are tightly intertwined, because identity without security is useless. And security is accomplished entirely through cryptography, because the centralized alternatives like locking all of your servers up in a closet don’t apply. Cloudy doesn’t do anything new cryptographically (wisely so), but for the benefit of those who aren’t familiar with it, here’s a superficial overview of the off-the-shelf tools I’m using: …
Continuing from Unstealthing, Incrementally.
I have many ideas for applications, but most of them seem to rely on similar kinds of infrastructure, in particular a distributed, secure application-level messaging system. Unfortunately, this doesn’t really exist yet, at least not in any form that meets my needs.
What am I talking about here? More colloquially, it’s a mechanism for letting applications all over the network send messages to each other, without requiring a central server, and without allowing messages to be eavesdropped upon or faked.
Let’s take it one buzzword at a time…
I don’t know about you, but I’m getting fed up with centralization. It happens because it’s the path of least resistance: buy a domain name, rent a server, buy more servers and stick a load-balancer up front as your user base grows. It’s solving problems by throwing hardware at them. The end result can certainly work fine, but too often it’s …
I got about 14 minutes of fame back in January with a blog post, wherein I grumbled about (among other things) how I disliked Apple’s culture of secrecy, and announced that I’d left Apple to work on my own, unspecified, project. In the intervening three months, I haven’t said anything about what that project is, almost as though it were … secret.
The irony of this is not lost on me.
Admittedly, there are things about my app that I do want to keep under my hat until they’re ready to show off in their full glory. I want to spend my one minute of remaining fame wisely; ideally accompanied by a large friendly “BUY NOW” button on my website.
But the main reason I haven’t been talking is just that I’ve been lazy. Well, not lazy, but focused on coding rather than talking. I’m mindful of a quote by (I think) John Crowley, which goes something like: …
Cabel Sasser, of indie developer Panic, reports from Japan:
"Within minutes of riding on the first trains in Japan, I notice a significant change in advertising, from train to television. The trend? No more printed URLs. The replacement? Search boxes! With recommended search termshttp://www.cabel.name/images-post/2008/03/search-2.jpg!
He goes on to note how common it is for people to type URLs or domain names into their browser’s search box instead of the address field. To American geeks this seems clueless, but Cabel points out that in Japan it makes more sense, since URLs are in a foreign alphabet, so search words are much more memorable. …
Arthur C. Clarke’s death hit me harder than other recent obituaries, even though it’s been decades since I read much by him. His were some of the first science fiction stories I read, at the age of ten or eleven; and for several years after that he was my favorite author.
I remember, during one of our long summer trips visiting the extended family in Germany, finding one of his story collections in the small English-language section of a public library. I read it over and over and over. I don’t remember which book it was, but it had some of his classic stories like “The Sentinel”, which became the inspiration of the film “2001”.
A bit later, it became my life’s highest priority to see that film. I had the novelization, and the making-of book The Lost Worlds Of 2001, and the soundtrack record (which itself was a big influence on me musically). But this was before video rentals, when you had to wait patiently for a movie to show up in a theater. Fortunately there were correspondingly a lot of theaters that showed older movies; but it still took months of poring over the newspaper theater listings before I finally found a showing of “2001” and dragged my dad to take me to see it. And it was worth the effort: I’d never seen anything like it. (This …
I had lost this historical document for a long time, but finally found it the other day on an old backup CD. It’s the original 1997 sketch I made of a chat user interface based on speech balloons.
Drawn in ClarisWorks, April 21, 1997. This was based on my experiences with MUDs and IRC, having a really hard time keeping track of many-way chats. I think the only IM app available then was ICQ, which I hadn’t heard of. (IIRC, AIM came out later that year, at least for non-AOL users.) This also predates Microsoft Comic Chat, which used speech balloons too, although in a very different UI: theirs was for novelty, mine was for usability.
Novel features that made it into iChat:
After digesting yesterday’s iPhone announcements [with fava beans and a nice Chianti] I started thinking about the pricing models made possible by the “Application Store”. In particular,
I think the answer’s clear. The Application Store will obviously be based on the iTunes store, whose bread-and-butter is a product, the AAC audio file, that sells for … 99¢. Apple’s clearly able to make a profit at that price point, despite credit-card processing fees, bandwidth costs, and comparable payments [Updated. Thanks, Dru!] to the record labels. So I see no reason they wouldn’t allow a developer to price an application that low.
But why would a developer want to sell an application for a net 70¢?
Micropayments …
The last paragraph of the poem “Systems” by Kristy Bowen:
“… I try to write a poem I wouldn’t want to sleep with. Would kick to the curb, wrap my thumbs around her slender neck and snap. This one’s still babied, blinking, wondering if it wants to be a skirt or a tire iron. Licking the perimeter of opened envelopes for a tiny bit of sweet. My nouns go awry every time I stop paying attention. Fall pretty like dimes on the sidewalk. My friend Melissa, whose name means bee-like, has a theory about systems. For every change in variable, the outcome shifts toward constant decay.”
—From [Brief History Of Girl As Match …
I’ve been thinking about writing an essay about the beauty & weirdness of cryptographic hash functions. The way any digitized data, however huge, can be named by a short fixed-size binary string. The way there are in theory an infinite number of hash collisions, but in practice zero. I was talking to myself about it, this morning, and two quotes appeared, which I write down here to remember:
“Hashing is my favorite computer-science concept.”
and
“”SHA“:http://en.wikipedia.org/wiki/SHA_hash_functions is the Dewey Decimal code of ”Borges’s Universal Library“:http://en.wikipedia.org/wiki/The_Library_of_Babel.”
(except that there’s a fallacy in the second statement, which I leave as an exercise for the reader.)
You can’t avoid asynchrony when writing network code, since operations can take an arbitrary amount of time, and often do. To keep the app responsive it has to be able to get other things done while a slow operation is in progress.
My first exposure to network programming was in Java, whose approach to asynchrony is to use threads. Lots of ’em. The API calls are [almost] all blocking, so you run them on background threads. This is good because it makes the way the API works more intuitive: you call a method, and it returns a value when it finishes. This makes your own code more intuitive, as it just performs the operations in order, like: open connection, send request, read response, parse response, close connection, return.
The downside is that making heavily threaded code work correctly can be very hard, and the problems are subtle, hard to understand and debug, and sometimes almost impossible to reproduce. Edward Lee’s paper The Trouble With Threads describes a complex Java server that was excruciatingly well-designed, code-reviewed and tested. …
I just ran across Invisible Games, a website of short and enigmatic fictions. One of them, The Loneliness Engine, reminds me of my own short-n-enigmatic We [Had Black Boxes]. No spooky synchronicity or anything, but they seem to belong together somehow … which itself fits in with the themes of both stories. Neat.
I used to think it was the Big Time if I got a link from Daring Fireball, but now someone just pointed out to me that the Fake Steve Jobs has taken note of my post.
So … what does it mean for my post to be criticized by a fictional construct that embodies a parody of the CEO of the very same ex-employer my post criticizes? Especially when, more specifically, that fictional construct’s humor is largely based on an exaggerated inversion of Apple’s carefully-groomed non-blogging public image, and he calls out a quote of mine that decries exactly the situation that his (fictional) presence repudiates?
Someone call the Semiotic Crisis Hotline for me! This situation calls for the skills of a Jean Baudrillard — too many levels of irony for me to parse, man.
I’ve been on my own for three weeks now, and I’m definitely enjoying it. I know that one of the general issues with self-employment is whether one can stay motivated without the external structure imposed by The Man. Fortunately I seem to have no problem with this — I’ve been coding at top speed. Mostly I work in the detached office, which is now clean and cozy, but sometimes I hang out on the couch in the living room. I have some Things running … they don’t look like much yet, but that’s because they’re infrastructure. This stuff ends up being harder than it seems it ought to, but I remind myself that if it weren’t hard, it wouldn’t be worth doing. And also: if it’s hard for me, it’s also probably hard for anyone else to do, which means less competition. ;-)
I’d like to thank everyone for their encouraging & thoughtful comments on my “Gone Indie” post. So: “Thanks!”. I just now turned off further comments on that post, because it’s been up a few weeks and the page is getting rather long.
I plan to write a few posts about what I’m working on, at a high level. I just don’t feel quite ready yet, mostly because right now my mind is more on how to make things work than on how to explain them. But the explaining is important too. …
Here’s a career update, for those of you who care: I’ve left Apple, and I’m now working on my own, from home, as an indie software developer. I have plans for at least two kick-ass Mac apps, I’ll probably contribute to a few open source projects, and I may dabble in some web stuff.
(At least, that’s the plan for now! Everything is subject to change without prior notice. This document contains forward-looking statements. These statements involve risks and uncertainties, and actual results may differ.)
This is kind of a big change for me. I’ve been continuously employed for 19 years, 16 of those at Apple. I clearly like being part of a team, part of a company, and specifically part of Apple. But there comes a time when a man’s gotta do what a man’s gotta do.
In fact, I was noticing the other day that there’s some… …
Santa has an early Xmas present for all you good Leopard programmers: GeekGameBoard, a new piece of sample code by the anonymous engineer elves at Apple.
[Update: GeekGameBoard is now an open-source project hosted at bitbucket.org
GeekGameBoard is an example of using Core Animation to present the user interface of a board or card game. It implements a small framework for implementing such games, with domain-specific classes like “Grid” and “Piece”, and examples of several game definitions built on top of the framework.
Some of the generally-useful Core Animation techniques illustrated are:
• Hit testing
• Dragging CALayers with the mouse
• Loading images from files and setting them as layer contents
• 3D “card-flip” animations …
In some online forums I list as interests both gnosticism and agnosticism, which is a bit of a joke since the two words are literally contradictory, but is true in that both are interesting and important to me. Agnosticism as my attitude toward religion: that the existence of a God or gods is fundamentally unknowable, undecidable, unprovable. Gnosticism as a mystic tradition, a suppressed early fork of Christianity, whose beliefs have more recently had a large impact on the literature of the fantastic and on postmodern philosophy (notably Philip K. Dick’s SF novels, the Matrix films, Philip Pullman’s His Dark Materials trilogy, and Jean Beaudrillard’s cultural theorizing.)
A few weeks ago I had the thought that you could combine Arthur Clarke’s famous Third Law with some of the ideas of Gnosticism, and arrive at a “proof” (which I’m aware is a contradiction in terms) of agnosticism. I’m sure this isn’t entirely original, but it amuses me.
Clarke’s Third Law states that “Any sufficiently advanced technology is indistinguishable from magic”. This idea has appeared in any number of science fiction plots, where time travelers from the future or astronauts visiting technologically-primitive planets are treated as wizards. It’s also been …
Warren just emailed me this photo, commemorating the release of the first Apple product I worked on. That’s me on the second row, second from the right, with the dopey expression (but no gray hairs.)
(click for humungous version)
I finally made myself a Facebook account, mostly to see what it’s like. Overall, I’m pretty impressed: the UI is nicer than most such sites, particularly the still-antiquated LiveJournal and the disaster that is MySpace. The biggest issue there seems to be that the main profile page absolutely doesn’t scale up to handle the exploding number of apps/widgets people are stuffing into it, so you end up with mile-long profiles containing box after box of junk.
But the most interesting thing I noticed is how the service has no visible identifiers for user identities. Unlike most centralized services, there’s no unique username to pick. I assume that, internally, each account requires a unique email address, but that address plays very little role in the user experience, apart from its use in helping people find their existing contacts’ profiles. The service does assign a unique number to every profile, and this shows up in profiles’ URLs, but it never seems to appear in the page itself. So there’s no obvious way to say “this is my Facebook ID”, other than pasting in the completely non-mnemonic URL of your profile page. And conversely, the visible identifiers you see for other members are simply their real names (plus photos/icons.) …
Paul Graham [who is obnoxiously elitist, but frequently insightful] has a new essay, “Holding a Program in One’s Head”, that is making me feel sad this morning.
(I’m fascinated by such spaces, as I’ve written before.) Currently my work is so fragmented into little bits — reading bug reports, figuring out what’s going wrong, making little tiny changes, testing them, dealing with the bureaucracy of integrating changes. It’s no one’s fault, and it’s a necessary part of finishing a large release, but I’m sick of it.
The worst thing is that I can’t even summon up the energy to focus deeply on anything else. When I’m not doing the above, I’m mostly sucking at the teat of incoming news-bites and emails. When all my unread counts hit zero I feel lost. I have any number of interesting in-progress projects I could work on, but I develop selective amnesia of them while at the keyboard, because I feel too lazy to put on those Goggles Of Omniscient Coding. …
We love to play the Hero — exploring dungeons, grabbing treasure, saving the world from evil. But I started wondering about the reasons behind some of the actions in such games, and especially about what my Heroic deeds looked like to the ordinary people of the lands I passed through. (As my wife once put it: “Why isn’t there a Hug button?”) The result is this story.
I don’t normally write this sort of antiquated prose, but the genre does require it. It was actually a fun exercise, and I’ve tried to affect more of a James Branch Cabell or Lord Dunsany voice, rather than the tiresome faux-Tolkien of most current heroic fantasy. …
I once had the idea of a charity that would collect discarded headsets from yuppies and distribute them to mentally ill homeless people. Just by wearing the headsets, they would eliminate the social stigma attached to talking to themselves on the street; this would help re-integrate them into society.
This tale of woe is making me rethink whether I want to be running any PHP-based software on my website.
Yes, integer overflows happen to the best of us (even those of us who write popular algorithm textbooks), but I would hope that once one is pointed out, the people maintaining the code would have a clue about how to fix it.
Stuff like “if (size>INT_MAX)…” is funny, but I find it even scarier that someone would think the solution to integer overflow is to store potentially-huge byte counts in variables of type “float”. Which is apparently still being done in top-of-tree PHP.
[Hint: “float” is almost always 32-bit IEEE format with a 24-bit mantissa, meaning it can’t represent any integer larger than 2^23^–1 (8 MB) exactly. And round-off error is the last thing you want when computing how large a buffer to allocate.]
Here’s my family recipe for apricot jam, handed down through generations. One generation, really — my mom got it from a pamphlet put out by some local womens’ group, after we moved to an old ramshackle house in the middle of a huge but disused apricot orchard. The trees were old, but a lot of them still produced fruit, and it was no trouble to walk around and collect bucketsful. So we needed some way to make use of all that fruit…
This recipe is different from the usual one you find packed in a box of pectin, because, well, it doesn’t use pectin. Instead, you thicken the jam by cooking it a lot longer. This means it tastes less like fresh fruit; but it has a wonderful taste of its own, a bit like dried apricots, and a nice gloopy texture. As a bonus, putting an apricot kernel[^1] in every jar gradually adds an almond-y aroma[^2].
Making jam is much easier (and safer) than most people think. After all, 100 years ago everyone used to can food, unless they were millionaire financiers or nomadic tribesmen. If our primitive ancestors could do it, so can you! And jam is easier than canning vegetables because the acidity of the fruit inhibits microorganisms, so you don’t have to be paranoid about sterilizing everything. …
This is a mix of post-punk (old and new). I made it about a month and a half ago, but hadn’t put together a cover until today. Now it’s ready…
[web page] [MP3] [more mixes]
Ever since Brent “NetNewsWire” Simmons posted his Thoughts On Large Cocoa Projects the other week, I’ve wanted to add some of my own tips. I’ve worked on some big projects (iChat, Apple’s Java runtime, OpenDoc) and have sometimes had to find my way around in others (Safari, Mail), so I know what Brent means when he says:
There’s no way I can remember, with any level of detail, how every part of [my app] works. I call it the Research Barrier, when an app is big enough that the developer sometimes has to do research to figure things out…
It’s been said many times that “the main person you’re writing comments for is yourself, six months in the future.” It’s always a good idea to keep that shadowy figure in mind while you code. Here are some other techniques I’ve found invaluable: …
NYT: Computer Science Takes Steps to Bring Women to the Fold
I find this article baffling and the comments on it aggravating.
“The nerd factor is huge,” Dr. Cuny said. … This image discourages members of both sexes, but the problem seems to be more prevalent among women. ‘They think of it as programming,’ Dr. Cuny said. ‘They don’t think of it as revolutionizing the way we are going to do medicine or create synthetic molecules or study our impact on the climate of the earth.’ …
My friend Tanya is a gateway to the strange and exotic worlds of fan- and slash-fiction. Today she pointed out a whole LiveJournal community, mac_hearts_pc, devoted to mostly-smutty extrapolations of Apple’s anthropomorphized Mac-vs-PC ads. Wow.
In her post about this, she says
“I tend to think of Macs as so feminine as to be, well, female”
which is really making me think…
How do we map computer behaviors onto ‘male’ and ‘female’? In American culture the æsthetic sense, intuition and readiness to please that exemplify “Mac-ness” bring to mind images of women, but if I challenge myself I can also imagine them as aspects of a courtly gentleman, like a royal servant or even a knight. Or perhaps of the British “gentleman’s gentleman”, such as Bunter or Jeeves … though here the details of the æsthetics don’t work, as this calls to mind a much darker, subtler UI theme, all leather, oak, brass and polished silver. The colors in Aqua fit better with the color scheme of medieval Europe or Japan. …
Figs cover the ground
The children step over them
Or sometimes they don’t
A hug and a kiss
A heart outlined with fingers
And a wave goodbye
To the very end
of the quivering green branch
clings a black squirrel
So much depends on
a red Mario beanie
left out on the lawn.
Yellow leaves dancing
in the air, two stories up
against green windows.
I cannot get up.
I am excused from all work:
Cat purrs on my lap.
The problem with writing about something I dislike is that, after the momentary pleasure of getting it off your chest, there’s not a lot of motivation to read people’s responses (especially the argumentative ones.) Better to pick as a topic something that I do like very much … such as music.
I can’t claim to be an expert on music: I can only barely play an instrument, my dj skills are wack, the theory hurts my brain, and my knowledge is encyclopedic only in a few micro-genres. But I’m rabidly enthusiastic about it; and fortunately, music nowadays is tightly entangled with computer technology, which (like any engineer) I can easily sound like an expert on.
And fortuitously, this month is open season on “open letters” on digital music. I thought SJ’s was pretty damn good really, probably better than I could manage; but fortunately many of the answer letters have set the bar so low that I think I can hold my own even though I’m neither a half-literate sports team owner nor a PR duckspeak generation algorithm. …
“I have verified that I can create a sound file that can wake Vista
speech recognition, open Windows Explorer, delete the documents folder,
and then empty the trash.”
— George Ou, ZDNet
Sounds like computer psychosis to me. “I’m sorry, Dave, but I can’t open that. The voices told me to delete all of your files.”
I went on a free-font-downloading bender last weekend. I still love typography, and I’m glad to see the arcane art of type design isn’t dying out. Back in the old days of Desktop Publishing, you had a choice between high-quality but expensive fonts from reputable foundries, or a bunch of cheap but crappy knockoffs done in Fontographer.
But now, thanks to mass amateurization, there are people who actually know what they’re doing, who design new typefaces for the fun of it and give them away. (The cannier ones give a few away as teasers and charge for the rest.) Collecting these makes for a fun evening once in a while, at least it does if you share my predilections. There’s the surprise of discovery, the glee of downloading it for free, and then later the avaricious satisfaction of organizing the fonts on your computer, like Scrooge McDuck running coins through his fingers.
The problem is that these days I don’t actually have a whole lot of use for fonts. Desktop Publishing is passé, I hardly ever print anything, and when I design something for the web I can’t use obscure fonts that other people don’t have. It’s frustrating! It makes me want to start a zine. …
It’s amusing how Steve Jobs’ remarks disparaging the idea of Java on the iPhone have ignited controversy. His point was, obviously, that the iPhone’s browser won’t support Java applets; which is a no-brainer because applets were killed dead-dead-dead by Flash and Ajax. But this seems to have riled up everyone who still cares about non-server-based Java, leading to the weird situation of seeing “Java” and “Mac” in the same sentence again*. Apparently some people still cling to the glorious dream of writing cross-platform GUI applications, waving tattered “Write Once Run Anywhere!” banners and clutching ‘Little’ Red Books with Duke’s picture on the front.
Me, I defected long ago. I’m another of those Apple Java engineers who dropped out. I spent five years as a raving Java fanboy, but I gave up after optimizing AWT, implementing drag and drop, and trying to make 1,200 pages of crappy APIs do the right thing on the Mac. Then I took a one-week Cocoa training course, and wrote the first prototype of iChat. …
I’ve always picked at my nails, bitten them, the cuticles too. A sign of nervousness, I know, and unsightly and unsanitary. Can’t help it, though. The nails, fingertips, are always growing, always in different configurations, and some of those configurations are just wrong, asymmetrical, with sharp bits sticking out. And I can’t leave those alone: I always think in the moment that I can peel off the wrong part and leave the nail smooth and right. But I really know that it almost always makes it worse.
Suggested background music: Frost - Steelwound
[audio:Steelwound.mp3]
I dreamed once, in high school, that my fingernails had turned to bone: spongy like the inside of a broken chicken leg, thick and jagged-edged. I didn’t touch them for a week after that, but the lesson didn’t last. I never learn, a fact that has become only too apparent in college. …
My friend Tanya asked her friends to write her a short bit of Slash fiction as a birthday present. Which is not something I’m accustomed to, but here goes…
>N
The Troll Room
This is a small room with passages to the east and south and a
forbidding hole leading west. Bloodstains and deep scratches (perhaps
made by an axe) mar the walls.
A nasty-looking troll, brandishing a bloody axe, blocks all passages out
of the room.
Your sword has begun to glow very brightly.
The troll swings his axe, but it misses.
>SWING SWORD
Whoosh!
The troll swings, you parry, but the force of his blow knocks your sword
away.
>INVENTORY
You are carrying a brass lantern, a key, an elongated brown sack
smelling of hot peppers, a bottle, and a heart-shaped box of chocolates. …
I dabbled in Interactive Fiction, aka Text Adventures, long ago —- I played Adventure on my Apple ][ and Dungeon/Zork on a VAX; I wrote a primitive game in BASIC and later in college partially implemented a language for building games in yacc; and then after graduating, my first serious Mac program was a souped-up and nearly finished version of that language. After that I was too busy with “real” jobs, but others kept the flame alive even after Infocom tanked, building their own adventure-design languages like TADS and Inform and spawning a cult scene of increasing complexity and literary merit. I kicked the tires of TADS and Inform a few years back, then got distracted by other shiny things. You know how it is.
Anyway: now I turn around and there’s Inform 7, a thing of splendor beyond my dreams. Not only does it have an IDE with a really interesting form of integration testing, but the syntax itself has become an ambitious attempt at natural language. I haven’t started coding yet — I have a dreamlike apprehension that the whole concept will melt like cotton-candy if I touch it — but as an example here is an unmodified section of the source code of a real game that I’ve just been playing: …
It just occurred to me that my newish MacBook gives me no less than four sensory modalities for detecting high CPU usage:
Still missing is taste, and maybe balance and proprioception, but I think I don’t want my computer using those pathways to communicate with me.
I had a tiny Linux
box
Its name was badtz-maru ;
It sat out in the office
Serving tunes for me and
you.
One day the Squeezebox
just went black!
I didn’t know what to do!
Safari, ssh and ping
Lost touch with badtz-maru.
The living room was silent
(Between games of
Pikachu).
Last weekend I rolled up my sleeves
And grafted on a head
So I could hack at badtz-maru
And raise it from the dead.
The boot parade scrolled by, but then
With sinking heart I read
Of errors in filesystems,
Evil things best left unsaid.
I grabbed my dusty Linux
book
And then without delay,
Lips moving with the effort,
Typed in ‘fsck’. …
Like most geeks, as a kid I not only despised the Cool Kids, but also wanted to be one of them too. My own school-age development trajectory took me from a state of total ignorance of what that required[^1], to brave attempts to fit in[^2], to a realization that different was cool[^3].
Anyway: these days being a Cool Kid is within every geek’s reach. Perhaps that’s because the shared culture has exploded into an uncountable number of fragments, each of which is a tribe with its own parallel hierarchies of coolness. Amen to that.
Within the confines of geekery, even if I don’t have a PGP key or submit patches to the Linux kernel or get Slashdotted, there are still subcultures of Cool Kids I can fit into.
One of my Geeky New Year’s Resolutions[^4] this year is to finally really learn Ruby On Rails, since it not only seems incredibly neat-o, but is also what all the cool kids seem to be into. So I bought Agile Web Development With Rails and have been plowing through it eagerly. I really appreciate that the book has both a lengthy tutorial and a series of later chapters explaining all of the components of the architecture in detail. I find that I learn best by reading about things in depth after getting my feet wet, and the …
I write code for a living. After all these years I still find it really exciting — I was instantly and permanently addicted at age 11, it’s just that the programs have gone from 20-line BASIC powers-of-two table printers, to enormous Java and Objective-C juggernauts — and moreover I’ve found it’s the one thing that I can work on consistently enough over a long period of time to finish a project of any size. My childhood was littered with unfinished stories, unfinished plans for undersea cities, unfinished D&D maps. But the programs got finished. (Most of the time.)
Herewith, entirely too much detail about the different programs people have paid me to write. Read on if you want, but you’re in the driver’s seat so feel free to hit that Back button if your eyes glaze over…
I went through the usual sequence of summer jobs, most interestingly three at Xerox where I wrote cool stuff in Smalltalk-80. There was a low point in ’87-’88 when I had just moved to Tucson and was intermittently under- and un-employed (which did give me the time to learn Mac programming and write an interesting compiler) but after that the career swung into action. …
Just when it seemed, a decade ago, that the programming world had settled on C++ as the lingua franca, the One Language To Rule Them All, instead we got an explosion of new high-level languages that have risen to popularity. Why did this happen? Chiefly because the World-Wide Web has conditioned users to expect five-second delays before any responses to their actions, which provides an environment ideally suited for interpreted, garbage-collected scripting languages. This movement has been encouraged by server vendors like Sun and IBM who are eager to show Web developers the productivity increases they can get by using such languages, especially after they then install massively powerful servers.
In addition to the mainstream scripting languages like Perl, PHP, Python, PavaScript, and Pruby, there are other ones that are less well known, mostly because their names don’t begin with “P”. I’ve been looking into several of these more obscure languages lately, partly because I hate doing the same things most other people do, but mostly because I love buying those O’Reilly books with the cute animals on the covers. …
Lua is an interesting scripting language. I can’t say I have much familiarity with it; I’ve only read the book, and a couple of papers, and downloaded and built the interpreter (which takes less than a minute). But what I’ve seen of it gives me a warm feeling, like reading a concise little poem, a haiku. It’s a small language, but what’s there is well-considered, and it appears that you can build bigger things (like object models, whether class- or prototype-based) out of its building blocks pretty easily.
The implementation of the Lua 5.0 runtime is also interesting, as described in an excellent paper. One of the smaller details that’s been fascinating me is that Lua, it turns out, uses unique string objects.
When you use any kind of garbage-collected (or ref-counted) framework, string objects accumulate like dust bunnies. I’ve profiled Java apps and seen tens of thousands of instances of java.lang.String. Cocoa apps also have large numbers of NSStrings lying around. Some of these are temporary strings that just haven’t been garbage-collected (or drained from an autorelease pool) yet; but I think a lot more of them are duplicates. …
Much of what I’m consumed with (at work) boils down to a question of: what is the right shape for the small but plentiful bits of writing that we are all creating daily? Here shape means largely visual representation but also sequencing and topology.
It’s a problem of hypertext, primarily. The World Wide Web established one shape for hypertext: individual pages with one-way links in the text, replacing one another in a back-forwards chain. It’s proven to be a pretty good shape, but it’s not the only one, and earlier thinkers like Engelbart and Nelson had lots of other ideas.
The texts I’m thinking of are, as I said, ‘bits’. Smaller than pages, mostly. Notes, posts, comments. Again, blogs established a shape for these: aggregated into [reverse-]chronological series of boxes on web pages, linking to their own pages, with [forward(!)-]chronological series of comments.
For a long time I’ve loved this idea of a vertical flow of boxes of text, each box big enough to hold its contents, no more. For a time, around 1988, I wrote people letters in the form of stacks of index cards, with a different thought on each card. After I finished the first release of Stickies, in 1995, I started to design a new version with …
Not pink yet, she: bloody red.
Not one to be held back, she, even by the host’s noose,
even by constraints of brute geometry.
Her universe distended, tore and bled for her.
Thus the advent of the smallest unstoppable force:
wee Alba hurled through the plate glass into life,
now fixes us with a blue gaze,
her raised arms encompassing it all,
and says “I am an old soul. I’m back now.”
This is one of my favorite interviews ever, and it reminds me of a long-gone era when the Cocteau Twins mattered, mattered really deeply, and were making music I could barely believe possible. Music I was not the only one to find wholly impossible to describe…
[Typed in by hand from a crumbly old copy of the November 16, 1985 issue of Melody Maker]
“In the best of all possible worlds,” said Robin, “this wouldn’t be happening.” Hold it right there. I’ve read this before. I don’t want any more.
“But…”
No buts. I’m determined that this will not be another Cocteau Twins interview about how The Cocteau Twins hate interviews because that, after all, after hours of agonised silence and blank incomprehension, is all that anyone’s ever gleaned from this lot on paper. I won’t sit down and discuss this again. I won’t attempt to defend the pathologically rigid rigmarole of the rock’n’roll interview, nor will I perpetrate it further. …
Way back in 1989 my friend M@ and I used to work at a font company called Kingsley/ATF Type Corporation. One evening after work — actually we were still at work, physically speaking — we began to consider the subject of anagrams of the company name. After running off the necessary letters (in 100pt ITC Galliard all caps from an Adobe Type 1 font, using Microsoft Word 4.0 on a Mac SE, printing to a 300dpi Apple LaserWriter NTX) and cutting them out (I forget the brand name of the scissors) we set to with gusto.
The results you can see below. Some phrases are innately anagrammable and some aren’t. KINGSLEY/ATF and KINGSLEY/ATF TYPE CORP had vast possibilities, some (SLAG TYPE FIN?) stretching the limits of comprehensibility, others (ALFKE GIN STY, ITSY FLAN KEG, TINTY SLOG) proving so useful that they worked their way into our daily conversation. I’ve highlighted my favorites in boldface.
KINGSLEY / A.T.F. …
Whose round soft dog fidgeting. Whose noisy laptop is on fire. Our round mp3 player falls. Whose stupid shining hairy bluish expensive white noisy mp3 player arrives. Any given odd shaped forg arrives as soon as his slopy pensil is angry at the place that his brothers stupid magazine stinks. Their well-crafted book run while whose white tv stinks and a given white mp3 player walks. His slopy binocyles stares at the place that a noisy ram lies. Her fancy baby prepare for fight. Any given beautiful soft bottle prepare for fight. Whose golden glasses stares the time that a noisy dog looks around. Whose red white bluish baby smells. His brothers little noisy dog is thinking or maybe a given soft tall printer adheres. A noisy book fidgeting. His brothers silver fancy odd shaped mouse sleeps. A given bluish balloon stands-still. A bluish glasses smiles however, mine fancy shining table is thinking. Mine tall green sofa stinks while his brothers white exam book is on fire. Her daughters silver expensive exam book lies and any smart table fidgeting. A given small bicycle lies the time that his brothers bluish sport shoes makes sound. Our bluish dog stares. A smart caw arrives as soon as his stupid soda makes sound and still her daughters white forg got an idea. Our fancy picture show its value. …
Time to bore you young whippersnappers with my early history in
computers. (I saw a couple of other people do it and thought hey! I can
do that
too First we have to set the Wayback Machine for the darkest depths of the '70s, a decade that's oh-so-much funner as retro than it was to live through...
Fall 1975. I’m in fifth grade. A couple of interesting logic-puzzle worksheets manage to get me interested in math, which has until now been a wasteland of times tables to tearfully memorize. My mom takes me to a nearby place called Creative Publications that published these worksheets, and I get a couple of books and math toys and their catalog.
November 1975. I ask for an interesting sounding book from the catalog for my birthday, and receive it. It’s called My Computer Likes Me When I Speak In BASIC. I devour the book and am blown away by the idea of programming a computer, although I may never actually set eyes on one. …
The Simple Mail Transfer Protocol is by no means perfect — its lack of authentication is a prime reason why spam is such a problem — but I think it got one thing right: it has the right topology for building a person-to-person communications system.
Most current non-email communications topologies are polarized at a few extremes:
The problems with centralized and isolated systems are pretty obvious: they don’t interoperate and they don’t scale well without heroic measures (AIM uses a server cluster capable of routing a billion IMs a day.) Peer-to-peer is extremely trendy, but it has its own problems: connectivity (firewalls and NATs make it hard for end users to contact each other) and availability (you can’t receive data unless you’re online.) …
Yesterday I got acquainted with our leaf-blower. It’s electric, thank Cthulhu, but not what you’d call “whisper quiet”. We got it as a gift several years ago, and I tried it once back then and it just blew the leaves into a huge swirling cloud that settled down exactly where it began. So I disappointedly put it in the shed and forgot about it.
This time, though, I treated it as if it were some new and powerful item from a game. The controls seem simple — just press the A button to turn it on/off and rotate the C stick to point it, kind of like Luigi’s Mansion — but it takes time to master. Here’s my brief player’s guide:
Anywhere near a wall you get the howling leaf tornado that I experienced before; I’m not sure if this is a bug or intentional, but avoid that. The brick patio was the best surface, though I had to evade obstacles like the picnic table to get those elusive remaining leaves for bonus points. The limited length of the extension cord added an element of strategy, as I often had to retrace my path to unwind the cord from around trees and posts. …
…each of us had a little box. We didn’t know each other, not at first; we weren’t even aware of each other. “We” was a grouping defined solely by the fact of our having these little boxes. Each box was black lacquer and about two inches on a side. A network of fine black raised lines covered it. The lid could be opened, revealing nothing much inside.
To be honest, it was hard to remember what was inside after you shut the lid. Sometimes people would look inside, shut the lid, then look inside again because they couldn’t remember what was inside. They’d repeat this process for minutes or hours at a time until someone kindly distracted them. Anyway, whatever was inside the boxes, sometimes it talked to us. Usually it would name a place to go. It didn’t make much sense for a while, but all the time the boxes were gradually bringing all of us closer to each other.
Then the instructions started to change. They still didn’t make much sense, but now we would walk around and see something like … like a couple of Coke cans stacked on top of each other, or a blue circle spray-painted on a wall, or a trash can set on fire, and we’d know that another one of us had done it. But we never saw each other. After a few weeks of this, each of us could tell there were hundreds of us all in the same neighborhood. We were each so excited because we had a pretty …
…we decided that staying awake as late as possible was the way to write new and creative things. This to be accomplished without the aid of stimulants since the goal was to be as sleepy as possible. In ideal circumstances we would actually fall asleep while typing without stopping, finding ourselves squatting in a gray hypnogogic landscape still tapping on the keyboard finishing up priceless new thoughts. The dream-laptop could then be carried along throughout the night as a powerful and modern spirit guide, helping us to keep appointments with buried archetypes and instantly add new dream symbols to our address books, in addition to the obvious utility of taking dictation during the dream, before the veil is torn on waking and the dream story scattered. The major obstacle was the discovery that waking has the same effect on the laptop as on the mind, leaving the hard disk fragmented and the contents of RAM corrupted, necessitating re-installation from a backup. The solution was to email or IM dreamnotes before waking, a nerve-racking business since the passage of realtime during dreams is so uncertain, and any moment might bring the noise of the alarm. We would therefore type our dreamnotes directly into the mail or chat window, leaving one finger always poised to tap the Send keystroke should we be startled awake. Proper proxy server setup was key, since strange firewalls surround the dreamworld, and the outgoing messages often took unconventional routes. On waking one learned to expect their arrival in places like fortune cookies or smudged flyers handed out by bored youths …
The apricots are falling, bit by bit
helped along by interfering squirrels.
Though not yet ripe, they roll upon the bricks,
all with tooth-marks, some with chewed-up pits.
This fruit debacle fills us with dismay,
as we had hoped the ripe fruit to preserve
and so retain the sweetness of the day
In far December when light’s gone away.
Arranged on a torn out page,
silver “S”s of old wire pulled from broken clocks.
A razor shadow scratched by halogen behind each,
tracing its shape in intersections with blue ink lines,
a curve modeling stresses and crystal faults.
Exhausted by years of funneling pulses from a quartz chip,
the wires relax now bit by bit,
slow motion snakes,
emitting sub-audible scritchings against the paper fibers.
As it unwinds, each proudly imagines itself a mainspring.
The Zen master Yoshi was playing a video game. Seated in the lotus position, he expertly maneuvered the controller with his gnarled hands. Nevertheless, on the screen Mario failed to leap from one block to the next and plummeted screaming into the void.
Again, Yoshi began the same level. Again, the moving platforms eluded the sprite onscreen.
Seventeen more times, master Yoshi caused the hapless plumber to fall into nothingness and lose another life.
Still, his pose remained serene, and a bud of a smile played on his lips.
At last the novice Ohta, who had been watching the whole time, could not contain himself. “Master,” he blurted out, “how can you remain so calm in the face of so excruciatingly difficult a level? Even when the platforms evaporate into thin air when you are yet a split second from reaching the Shine that is your goal? How do you restrain yourself from throwing the controller through the nearest shoji?” …
We are all snakes. We have a tail and onetwothree mouths. The middle mouth bites the tail to hold fast to form, to keep the extra blessings from dropping off one end and becoming lost in the untidy æther. Leftright mouths are perhaps free to latch onto other snakes should the local geometry and snake density so permit. When our fangs sink into each other we exchange blessings. It must be so. Blessings endlessly recirculated become stale, they need another blood type in which to flow for a time before being returned freshly laundered and creased & giving off a pleasant aroma of incense.
Eli finally entered the Fulfillment Center at dusk, through the wide metal doors opening into the chilly space within. He had been waiting in line since dawn, shuffling slowly back and forth through the cracked remnants of the old parking lot under the eyes of the security guards. The Center was an old, damaged warehouse – this had been an industrial area before the war – and was lit within by banks of fluorescent tubes suspended from the high ceiling.
Once inside he waited briefly before stepping up to one of the many card tables set up in a line near the door. A tired looking young man checked his ID card, walked back to one of the many large crates filling the space, rummaged about inside, and returned with a small cardboard box.
“You’ll have to sign for it,” the young man said mechanically, sliding a clipboard across the table. Eli did so, using the ballpoint pen chained to it, and picked up the box as he slid the clipboard back across the desk. …
By way of introducing my favorite hypertext, I have to digress a bit. Last March [2001] I had a particularly nasty flu for about three weeks, which ended up as a wretched dry cough. I couldn’t go one minute without coughing, and I had a horrible sharp pain in my ribs caused by a sprained chest muscle. One night I was lying on the couch (so I wouldn’t keep Diana up all night) trying in vain to sleep, and decided to look up exciting Drug Facts about various medications I was taking. Guaifenasin wasn’t very interesting (just an expectorant, toxic in large doses) but Dextromethorphan turned out to be fascinating stuff – chemically similar to opiates, it suppresses coughs but doesn’t bind to any opiate receptors. What the mainstream medical websites don’t tell you, however, is that it does have very potent psychedelic effects at large doses. I’d heard about people getting stoned on cough syrup and assumed it was just codeine, but no, DXM is quite odd stuff in its own right.
Disclaimer. I would never try high doses of Dextromethorphan myself and don’t recommend that you do. Not only does chugging cough syrup sound disgusting, but DXM can become addictive, and the long term effects are known to include brain damage. Of course, that doesn’t mean we can’t safely enjoy ourselves by reading about other people’s unwise use of this interesting drug! …
We stepped out our back door into splendor:
– the rain-choked hills casting off their muddy carapace of topsoil
– uprooted trees shedding their last dead leaves like ticker-tape
– all of up heading for down.
All the wet rot of the rotating Earth converged on our yard
but was held back by cinderblock walls
with a splash.
Our house lay alone at the foot of a brown slope devoid of landmarks:
a virgin field of stumps, poles, and spinning tires.
Anything might be planted in that field and grow.
Any possibility might be granted in a new equilibrium.
Like two children we held hands and stepped over the wall,
digging our bare feet into dark humus, taking root.
The horizon folded down its blackness.
Overhead curled exalted green clouds
of Sun-born particles spiraling in.
Now upward in an arc, tied to the long invisible armature of the Pole,
flew my humble cardboard tube of Earthly minerals,
in one moment transmuted into circlets and spheres of sparks —
dark materials achieving by dint of effort
glory surpassing the Sun’s electrons,
if only for a second.
Hood thrown back I howled a warning to low-flying angels.
The dogs lay panting in the snow, unimpressed.
System Software were looking for a Post-It Notes™ type of program for System 7.5. They were already buying several other utilities — including Find File, Scrapbook, SuperClock — from third parties, and offered Antler Software (me) the same lump sum deal for the “Antler Notes” utility I was working on. It was a nice piece of change. I was happy.
This came to the attention of certain people in upper management, whose conclusion was (I’m paraphrasing here) “Why are we going to pay for this? This guy works for Apple — we already own his program!” You can imagine an evil cackle here if you like; I certainly did at the time, although I’ve mellowed a bit since.
For a while it looked as though Apple was going to get Antler Notes / Stickies at no cost — wotta deal! As it happened, however, some of the nice people mentioned earlier in this story arranged for me to get a bonus, not officially in any way related to Stickies of course, but it made me feel better. …
The problem of leisure
What to do for pleasure
Ideal love a new purchase
A market of the senses
—Gang Of Four, “Natural’s Not In It”
“He realizes everything he does is second-hand, a waking dream, a dream someone else has dreamed for him — when he walks into a pub and greets friends with a line he’s half-consciously lifted from last night’s sit-com, he’s an advertisement. He hears himself and he feels tricked, humiliated, so he smashes into his friends … as if he’s never seen them before but knows they mean him no good. Screaming, he insists that he’s happy.”
—Greil Marcus …
I decided I would only work on this page after ten PM, when I think differently. When I’m tired but alert, and everyone around me is asleep, and it’s dark and quiet.
The cognitive scientist and AI researcher David Gelernter has a model of consciousness that has focus as its parameter: varying focus produces mental states from rigorous logical thought (when focus is at its highest) all the way down to dreaming (when focus is at its lowest.) In high focus states the mind seizes precisely on individual concepts and ideas. In low focus states, multiple ideas, concepts and memories overlay each other such that they can’t be distinguished; they’re superimposed and common features line up, connections between disparate thoughts. In this mode the mind jumps from one memory to another, linked by a chain of connections formed by lining up fragmentary images of those memories. Like a dream.
The book I hold most dear is John Crowley’s novel Engine Summer. In it, there is a society called the Truthful Speakers who have a sort of Utopia. They have an understanding of personality and of interpersonal relationships that allows them to untangle mental problems and conflicts with the same degree of rigor and confidence with which we tackle technical problems. This understanding and the techniques through which it is implemented are never made clear (the book would be far less …
The beach that fall was overrun by glass lizards; I had never seen them before. I knew there had been none at the beach when we had visited during the summers (I could remember four summers, and my parents said there had been more.)
In the summer the sand was hot, the evenings cool, and our whole camp stayed for a week to catch the foot-long azu as they swam to the beach and flopped out of the water onto the wet sand. It was easy to catch them as they lay there: we children chased them with nets, while the adults favored spears that we were not permitted to touch or come near. Netting the fish was fun, but we all envied the adults for the elegance of their swift downward strokes pinning the fish to the sand. I was too young to feel much sympathy for the fish, or wonder why they came to the beach so suicidally. Fortunately the adults did, and made sure that enough fish survived to spawn and return the next year. But this was fall, the weather cooler and the azu safe at sea, and I came alone with my parents.
The lizards were new to me. I saw the first only after I stepped on it as we jumped down from the floater. It crunched beneath my shoe like a fragile holiday ornament, and as I picked up and examined the brittle pieces my father told me not to go barefoot on the beach or I would hurt myself. I half-listened, wondering at the detail of the shape and why …
WHEN I stick my head out of the skylight and look to the left I can see the Cow Telescope atop its hill, red light at the tip blinking to ward off low-flying aircraft. You can see it from Interstate 280; from the back of my parents’ Volvo I used to watch it as we drove past, a big metal parabolic dish pointed at something in the sky, on a grassy hill alone except for the odd ruminating cow. And so it was obviously the Cow Telescope, searching for radio emissions from peaceful cow civilizations across the galaxy — civilizations that might have the answers to problems like flavorless grasses, painful udders or the great mystery of being ground up into hamburger. The cows built their radio telescope in secret, and hope that no one will notice it on that hill, or that those who do notice it will attribute it to bearded Stanford researchers, the same ones who stretched a linear accelerator underneath the freeway where electrons doing 99.9999% of the speed of light excite the thoughts of motorists who would eagerly match them in a chicken-race if only the slowpokes ahead of them would get out the damn way — the slow cautious drivers with hats on, hats covering their horns, badges of their secret cowness, waving them with a surreptitious toss of the head at their gallant compatriots, as they cruise slowly past the blinking light of the Cow Telescope. …